Guest Blog: Cyber risk and cybersecurity: A systematic…
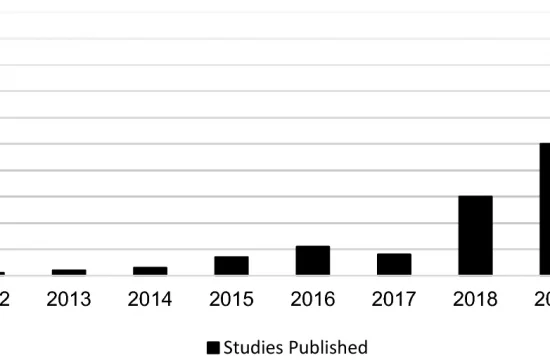
The following article is a guest blog by Frank Cremer, currently a PHD candidate at the technical University of Cologne about his and his co-authors newest paper, systemtically tabulating and reviewing existing cyber risk and…